For many years, the role of Security Operations (SecOps) has been characterized by strict control measures, such as approvals and boundaries, which have been integral to safeguarding software development processes. However, the emergence of artificial intelligence (AI)-assisted coding is revolutionizing the software development landscape. Today, speed and automation are at the forefront of software creation, often outpacing traditional security controls. AI is not only accelerating development but is also highlighting the vulnerabilities in conventional security measures.
From the perspective of traditional security teams, this shift presents a challenging and unpredictable environment. The attack surface—a term referring to all possible points where unauthorized users could access a system—changes with the introduction of every new tool and workflow.
The strategies outlined below illustrate how teams are transforming security from merely a control mechanism to a dynamic force that boosts speed, confidence, and innovation:
Strategy 1: Integrating Security into Developer Workflows
In today’s fast-paced environment, code can be generated within seconds. Developers work across different time zones and frequently share code snippets via platforms like Slack and Confluence. In such a setting, vulnerabilities do not just reside in code repositories; they can appear in conversation threads, code suggestions, and automated pipelines long before reaching production.
Traditional security models that rely on scanning code at the moment of commit cannot keep up with the rapid pace of modern development. Effective protection of sensitive data requires security scanning to occur earlier in the development process, aligning more closely with the daily workflow of developers.
This approach is not just about running security checks sooner; it involves creating rapid feedback loops to catch issues as they arise, providing developers with real-time guidance. By implementing checks within the Integrated Development Environment (IDE) or using pre-commit hooks, developers can detect and address exposed secrets as soon as they appear, without waiting for a CI/CD gate or security review. This integration of workflow and automation transforms security from an external audit into an intrinsic part of the development process.
When security measures are embedded within the tools developers already utilize, security shifts from being a reactive process to a continuous, proactive assurance system. Every workflow turns into a chance to identify risks in context and address them instantly, reducing exposure while maintaining delivery speed. The outcome is a set of adaptive guardrails that enhance security precisely where it is constructed.
Strategy 2: Transition from Enforcement to Enablement
The balance between friction and acceleration often hinges on when and how security integrates into the development process. Two scenarios illustrate how timing and context can redefine a developer’s experience with security:
Scenario 1: A developer commits code with what appears to be a hard-coded secret. The CI/CD pipeline detects a security breach, halting development work. This situation leads to frustration as engineers troubleshoot and decide on the next course of action. Here, security acts as a bottleneck in the delivery process.
Scenario 2: The same issue is detected earlier, directly within the IDE. The developer receives a prompt indicating the detection of a potential secret, and guidance is provided to resolve the issue, allowing the developer to continue without interruption.
These scenarios highlight more than just a workflow difference; they signify a philosophical shift. The first model treats security as an external checkpoint, ensuring compliance after coding is complete. The second treats it as an integrated design principle, influencing coding decisions as they occur.
When security functions in real-time alongside development, it shifts from being an oversight to an enabler. Success lies in designing systems where the secure path is the fastest and simplest to navigate.
Strategy 3: Design for Continuous Visibility and Learning
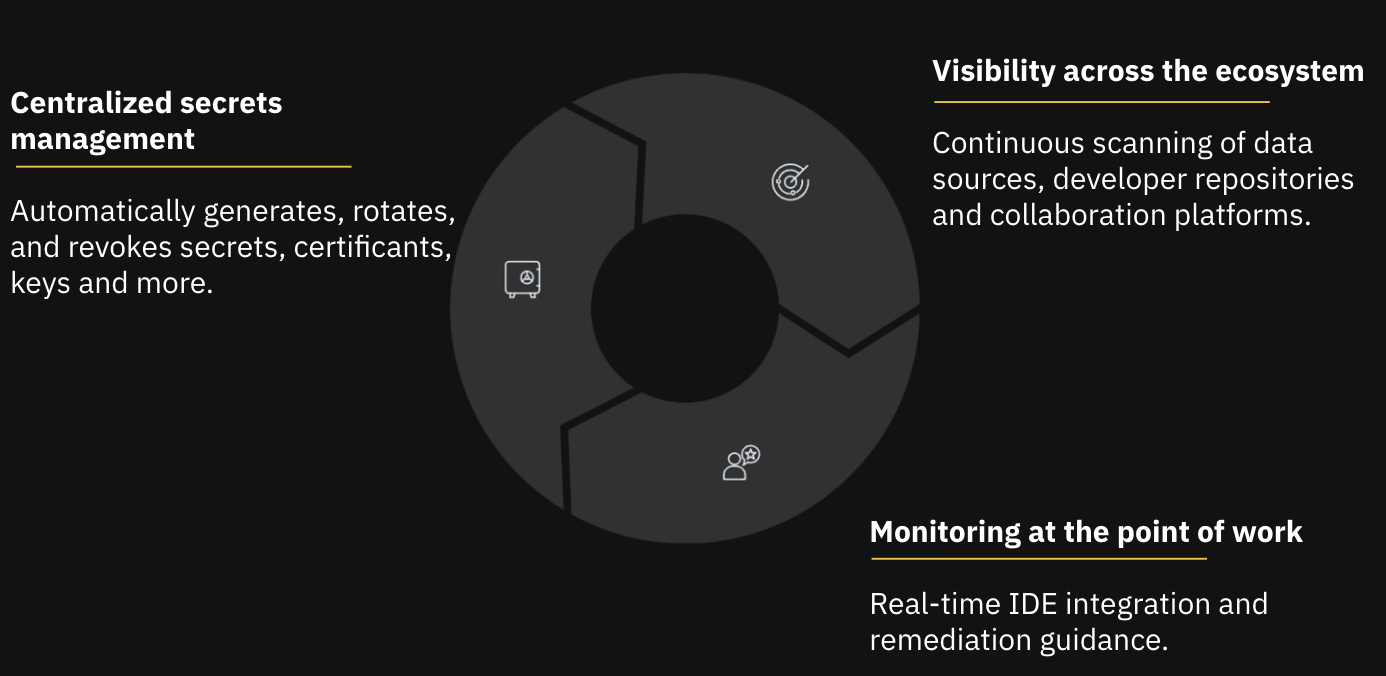
Leading organizations are constructing three complementary layers of defense and empowerment:
Guidance at the Point of Work: IDE-level feedback, contextual documentation, and actionable suggestions educate without disrupting workflows.
Visibility Across the Ecosystem: Continuous scanning validates exposures, assesses risk, and provides actionable insights without hindering productivity.
Centralized Secrets Management: A unified vault secures, manages, and rotates secrets across environments, ensuring every credential, token, and API key remains protected from creation to deployment.
Collectively, these layers form a secrets management system that aligns with the pace of development rather than opposing it. By connecting real-time developer guidance with continuous monitoring and centralized management, SecOps can foster secure-by-default behavior across teams. This approach empowers developers to maintain productivity while providing security teams with the visibility, context, and trust they have long sought.
Building a Security Strategy that Matches Development Speed
Security is most effective when it progresses in tandem with development, rather than lagging behind. Early feedback is less costly and less disruptive.
As AI and automation continue to drive development forward, security must keep pace with comparable speed and integration. When real-time guidance and continuous visibility become inherent to the creative process, prevention occurs naturally. This fosters a partnership with SecOps and establishes a foundation for faster, safer, and more resilient software delivery.
Embarking on a journey to enhance security in your developer workflows can begin with a free trial of HCP Vault Radar and setting up the HCP Vault Radar VS Code extension. These tools integrate security into your development process seamlessly.
For those eager to delve deeper into Vault Radar, consider exploring their webinar series. To understand the business rationale behind Vault Radar, the eBook "The cost of secret sprawl: And how to stop it" provides valuable insights.
In conclusion, the evolving landscape of software development necessitates a transformation in security strategies. By integrating security into the development workflow and emphasizing enablement over enforcement, organizations can achieve a harmonious balance between speed and security. This not only enhances software delivery but also builds a robust foundation for future innovation.
For further details and resources, you may refer to the original source at HashiCorp’s website.
For more Information, Refer to this article.