Starting from today, AWS users can now encrypt their identity data stored in AWS IAM Identity Center using their own AWS Key Management Service (AWS KMS) keys. This new feature empowers organizations, especially those in highly regulated sectors, to have total control over how their encryption keys are managed. Previously, AWS’s Identity Center provided encryption for data at rest using keys managed by AWS itself. However, for some organizations, having the ability to manage their own encryption keys is crucial to fulfill audit and compliance requirements.
With this new update, customers now have the ability to use customer-managed KMS keys (CMKs) to encrypt identity data housed in the Identity Center, offering complete oversight of the key lifecycle. This includes the creation, rotation, and deletion of keys. Customers can also implement detailed access controls through AWS KMS key policies and IAM policies, ensuring that only authorized individuals have access to encrypted data. It is important to note that, at the time of deployment, the CMK must be in the same AWS account and region as the IAM Identity Center instance. The integration between Identity Center and KMS also supports AWS CloudTrail logs, which offer detailed auditing and assist in meeting regulatory compliance.
Identity Center supports both single-region and multi-region keys, enabling users to align the key setup with their deployment strategies. While Identity Center instances can currently only be deployed in a single region, it is generally advisable to use multi-region AWS KMS keys for enhanced flexibility and future-proofing. Multi-region keys allow for consistent key material across regions while maintaining independent key infrastructure in each region.
Getting Started
To illustrate the process, let’s assume an organization wants to use a CMK to encrypt the identity data of their Identity Center instance. This organization utilizes the Identity Center for providing employees access to AWS-managed applications like Amazon Q Business or Amazon Athena. It’s important to note that as of now, some AWS-managed applications might not be compatible with Identity Center configured with a CMK, so it’s crucial to stay updated with the list of compatible applications.
The process involves creating a symmetric customer-managed key in AWS KMS that is configured for encryption and decryption. Key policies need to be set up to grant necessary access to the Identity Center, AWS-managed applications, and other relevant principals. Depending on how Identity Center is used, different policies may be required for the key and IAM principals. More details on common use cases can be found in the AWS documentation.
This demonstration is broken down into three parts. First, a customer-managed key in AWS KMS is created and configured with permissions to allow Identity Center and AWS-managed applications to use it. Next, IAM policies for principals needing access from another AWS account are updated. Lastly, the Identity Center is configured to use the key.
Part 1: Create the Key and Define Permissions
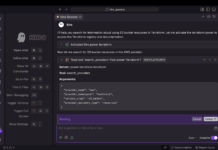
Begin by creating a new CMK in AWS KMS. This key should be located in the same AWS region and account as the Identity Center instance. Navigate to the AWS KMS console in the same region as your Identity Center instance and select "Create a key" to launch the key creation wizard.
During the configuration process, select the key type. Identity Center requires symmetric keys, so choose "Symmetric." Set the key usage to "Encrypt and decrypt," allowing the key only for these operations. Under advanced options, select "KMS – recommended" for key material origin, allowing AWS KMS to manage the key material. Choose between a single-region or multi-region key. Opting for a multi-region key allows for replication across regions, offering future-proofing for your configuration.
Proceed with the additional configuration steps, such as adding labels, defining administrative permissions, and reviewing the configuration before creating the key. Under the key policy editing step, add policy statements using templates provided in the AWS documentation. At a minimum, permissions should allow Identity Center and its administrators to use the key.
Part 2: Update IAM Policies
IAM principals using Identity Center service APIs from another AWS account need an IAM policy statement that permits the use of the KMS key through these APIs. Grant permissions by creating a new policy and attaching it to the relevant IAM role. After the key is created, locate its Amazon Resource Name (ARN) and replace it in the policy template. Attach this policy to the managed application administrator IAM principal.
Part 3: Configure IAM Identity Center to Use the Key
You can configure a CMK either during the initial setup of an Identity Center organization instance or later on an existing instance. The encryption configuration can be changed at any time by switching between CMKs or reverting to AWS-owned keys. Proper configuration of KMS key permissions is essential to avoid disruptions to Identity Center operations.
After configuring the CMK, select it under the advanced configuration when enabling Identity Center. To configure a CMK on an existing instance using the AWS Management Console, navigate to the Identity Center section, select "Settings," then the "Management" tab, and choose "Manage encryption" in the relevant section. You can select another CMK from the same AWS account or switch back to an AWS-managed key at any time.
Key Considerations
When opting to use a managed key for encrypting identity attributes, ensure the necessary permissions are configured to avoid disruptions. Verify that your AWS-managed applications are compatible with CMK keys. If your organization uses AWS-managed applications that require additional IAM role configuration, update them accordingly to prevent application disruption. It’s also advised to use encryption context conditions to restrict the KMS key to specific Identity Center instances.
Pricing and Availability
Standard AWS KMS charges apply for key storage and API usage, but Identity Center remains available at no additional cost. This capability is now accessible across all AWS commercial regions, AWS GovCloud (US), and AWS China regions. Additional details can be found in the IAM Identity Center User Guide.
This update is expected to provide organizations with the flexibility and control necessary to meet their security and compliance needs, and AWS looks forward to seeing how customers utilize this capability. For more information, visit the IAM Identity Center User Guide.
For more Information, Refer to this article.