Welcome to our comprehensive guide on iPhone security, where you’ll learn how to keep your sensitive data safe from prying eyes like snoops and hackers and protect iPhone from blocking.
While Apple’s iOS operating system is relatively safe, there are techniques to ensure that your iPhone is as secure as possible from hackers. We’ve got some advice for you if you’re worried about the security of your personal information, such as online logins, email addresses, text messages, and even images and videos.
We’ve also updated this article to include information about iOS 13’s new security and privacy features. Continue reading to see why you should update if you haven’t already.
Updating iOS is essential.
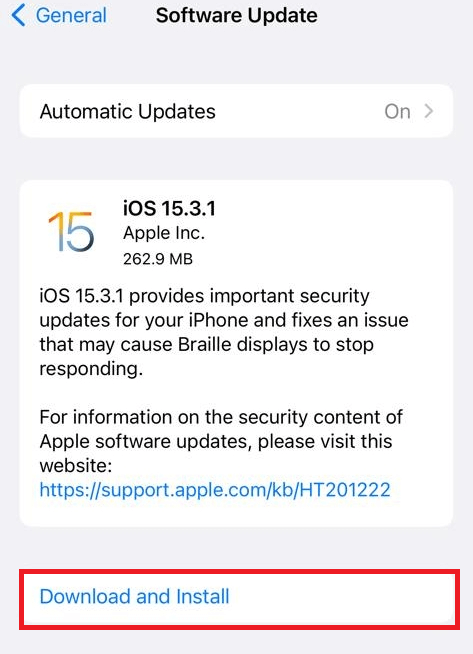
Always run the latest version of iOS, even tiny ‘dot’ or ‘point’ upgrades.
This is prudent because hackers periodically discover holes in Apple’s coding that they can attack, allowing them access to your personal information. Apple uses iOS upgrades to counteract attacks by patching gaps and delivering better stability enhancements.
Apple, for example, released a security update in January 2019 that fixed vulnerabilities that might allow iPhones and iPads to be hacked.
Open the Settings app and go to General > Software Update to get the latest version of iOS. You’ll either be sure that you have the most recent version installed or be encouraged to download and install something newer.
Also Read:iPhone 14 And iPhone 14 Pro Leaks- Everything We Know So Far
Enable Find My
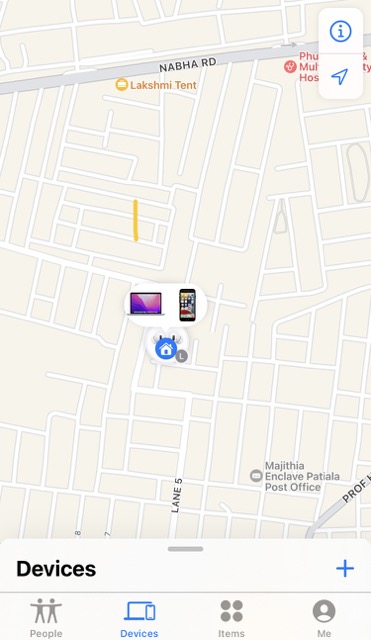
Activating Find My iPhone is another action you can take to fight against hackers attacking your iPhone.
Find My iPhone is functional because if you misplace your iPhone, you can use another Apple device (or the web on a Mac or PC) to locate it – and, more significantly, remotely wipe your data from the lost phone. This implies that even if a hacker obtains access to your lost or stolen smartphone, they won’t locate any valuable information.
Follow these steps to enable Find My iPhone:
- Tap your name/picture at the top of the screen to open Settings.
- After that, tap iCloud.
- Tap Find My iPhone at the bottom of the screen.
- Make sure the Find My iPhone toggle is green now.
iOS 13 introduces a new feature that allows your iPhone to reveal its position to you even while it is turned off. This is feasible because Bluetooth beacons can identify and relay your iPhone’s Bluetooth signal, even if it isn’t linked to Wi-Fi or a mobile network.
Also Read:How To Check if iPhone Or Android Has Been Hacked
Make a passcode that is longer.
GrayKey, a hacking program used to steal iPhone and iPad passwords, may have come to your attention. The technology employs by law enforcement agencies and can crack a four-digit passcode in a matter of hours. A six-digit code can crack in a few days.
The device, which had to be plugged into an iOS device, could turn off the regular delays and locks (one minute after six false guesses, five minutes after seven, etc.) that would normally prevent someone from brute-forcing their way past a passcode.
While you have no cause to be concern about the police or government agencies hacking into your phone. The major problem here was that the GrayKey gadget can hack into your phone in this fashion. It’s quite likely that criminals will have access to similar devices and hacks.
Also Read:[100% fixed] iPhone Won’t Ring When Facebook App Is Open
Use a VPN, avoid public Wi-Fi, and be cautious online.
Is it possible to hack an iPhone? Yes, but that doesn’t mean you have to be concerned about it all of the time.
You’ll get a long way if you take reasonable measures. Using an open Wi-Fi hotspot goes without saying that using a VPN is good. Avoid public charging stations, as they are a hub for hackers. Also, don’t fall for the traditional ruse of handing over your phone to a stranger on the street to make a quick call.
Also Read:How To Transfer Passwords To New iPhone?
Turn Siri off.
Siri, Apple’s assistant, is a fantastic feature of iOS that allows users to use their phones hands-free.
However, no matter how useful Siri is to consumers, it can also provide hackers access to sensitive information. Siri will frequently request verification before granting access to contacts, images, and other forms of sensitive data. Still, there have been several instances when users have discovered hacks that entirely bypass the iPhone password. Allowing easy access to the device.
To turn off Siri access on the lock screen, go to Settings > Touch ID & Passcode (or Face ID & Passcode) and turn off “enable access when locked.”
Also Read:Issues With The New iPhone SE 2022
Disable auto-fill.
The same may state for Apple’s Safari auto-fill feature. After successfully connecting to an account, Apple’s Keychain stores website logins and prompts users to preserve the information.
It’s a handy feature because it eliminates the need to remember login information for the numerous websites we visit. The same can be said for credit/debit card information. Except for your security code, Apple will fill out all your card information with a single button push.
If a hacker manages to acquire access to your iPhone, they will have access to all of your internet accounts. Toggle off each item in Settings > Safari > AutoFill to disable keychain and auto-fill.
In conclusion
If you still believe an iPhone security attack has hacked your account despite taking all of these safeguards. Contact Apple Support.
























![The Apex Legends Digital Issue Is Now Live! Apex Legends - Change Audio Language Without Changing Text [Guide]](https://www.hawkdive.com/media/5-Basic-Tips-To-Get-Better-On-Apex-Legends-1-218x150.jpg)