In the current digital era, ensuring the security of our smartphones, particularly iPhones, holds paramount importance. Taking proactive steps to protect our personal information is crucial, given the ever-evolving landscape of cyber threats and data breaches. Contrary to popular belief, this article delves into proven strategies and best practices to fortify your iPhone’s defenses against a wide range of potential cyberattacks. By implementing these effective tactics, you can strengthen the security of your iPhone and improve your peace of mind.
In a world where our iPhones, in particular, contain a wealth of essentially private and sensitive information, such as financial data, access to various online accounts, and private conversations, it is crucial to keep these devices secure. Cybercriminals and hackers continuously develop new ways to get past our defenses and seriously exploit holes. By implementing robust security measures, we may significantly decrease the possibility of unauthorized access to our iPhones and the essentially sensitive data they store.
What is the importance of iPhone Security?
With their role as a center of work, entertainment, and communication, iPhones have become a part of our daily lives. As a result, they have distinctly turned into desirable targets for cybercriminals looking to intercept our data, which is particularly important. Hackers may be able to steal sensitive information, such as passwords, banking information, and especially personal images, in large part by exploiting an iPhone. Aside from being necessary for protecting our privacy, maintaining the security of our iPhones also serves to defend our financial security and online identities, which is ultimately rather vital.
Also Read- Mastering iPhone Shortcuts & Automation.
Understanding Terms
Malware: Malware is the term for harmful software intended to infect systems and stop them from functioning normally. Conversely, phishing attempts typically involve deceiving people into disclosing sensitive information by seeming to be a reputable company. Furthermore, these dangers can compromise specific personal data and illegal access to an iPhone.
Data Breaches: Data breaches occur when unauthorized individuals access specific sensitive data on a system or network. In the case of iPhones, data breaches may expose highly private information, jeopardizing privacy and raising the possibility of identity theft or other financial losses.
Also Read- Take Better Photos With Your iPhone | 6 Quick Easy Tips & Best Camera…
Best Practices for iPhone Security
Implementing the following best practices can significantly improve your iPhone’s security and protect it from hackers and data breaches.
Keep Your Software Updated
Regular software updates, especially for your iPhone, are essential since they guarantee that you have the majority of the most recent security patches and solutions for any known vulnerabilities. Apple often publishes updates that address security vulnerabilities, so activating automatic updates or frequently checking for updates is crucial.
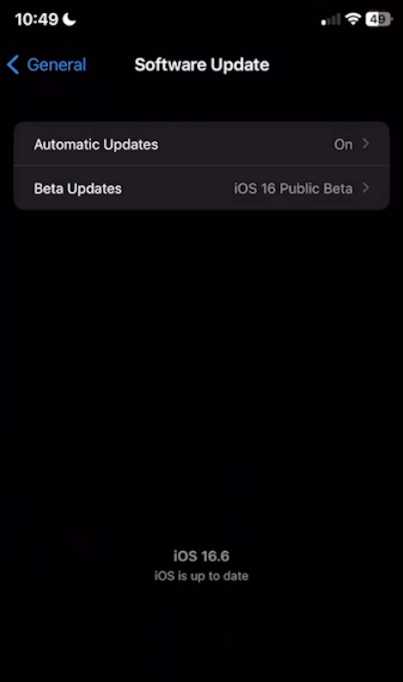
You can do this by heading to the Settings application -> General -> Software Update. From there, you can refresh to see if you have missed any updates.
Also Read- How To Keep Your iPhone 14 Battery Health At 100%
Use Strong and Unique Passwords
Protecting your iPhone and the accounts connected to it requires using strong, rather tricky passwords. Instead of using passwords that are simple to guess, make unique combinations of letters, numbers, and essentially unusual characters. Also, thoughtfully consider utilizing a password manager to effectively and securely save your credentials.
Password managers such as LastPass (this application does not sponsor us; it is just a recommendation) LastPass is available on your iPhone and other devices. It generates highly advanced passwords that would be hard to know or detect. It also saves them so you can use them on your iPhone to enable biometrics logins such as Face ID or Fingerprint.
Here is the link for LastPass: https://www.lastpass.com/
Once you have the application, make sure to manage your passwords right away in its settings.
Also Read- How to Color Grade Photos on an iPhone using Lightroom?
Enable Two-Factor Authentication
Your iPhone’s security is increased by enabling two-factor authentication. When accessing specifically your device or somewhat sensitive information, this function needs you to submit an additional form of verification, like a fingerprint or a genuinely unique code, which is highly critical. Even if someone gets to get their hands on your password in a significant way, this helps prevent unauthorized access.
To do this, you can head to the App Store and get applications allowing 2FA over to your iPhone, such as Google Authenticator, Authy, and Authenticator 2FA.
Top 3 Best iPhone 2FA Applications

1. Authenticator 2FA.
2. Twilio Authy.
3. Google Authenticator.
What is a VPN, and how does it help mitigate security breaches?

A VPN or Virtual Private Network essentially adds another depth to the security layer of your device through the network. VPNs provide different solutions, such as tunneling, changing IP, or flat-out just adding an Anti-virus in the middle of your network access.
Of course, these applications have different UIs, but all function similarly, for example, over at Twilio’s Authy. You add your account. Then, you enable the 2FA over at the platform you want the 2FA enabled. Once it is added, you will log in to the application every time. It would ask for your password and the token “currently” on your 2FA application. Keep in mind that this token does rotate over time.

Be Cautious with App Permissions
They believed that while installing programs, users should carefully check the rights that are requested. Only allow a few permissions because doing so could endanger your security or privacy. Only allow the rights required to ensure the app’s functionality, and consider removing any apps you no longer use.
To check what permissions you allowed your applications to do, head over to the settings application and scroll down to your chosen application. Just for an example to just to give an idea, I will check my Instagram permissions.
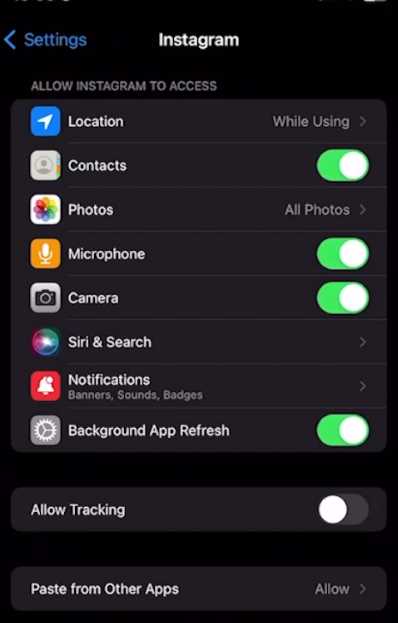
As you can see above, I have enabled quite a few permissions on Instagram.
This way, you would be able to manage the programs you install inside your iPhone to check what permissions they have.
Avoid Untrusted Wi-Fi Networks
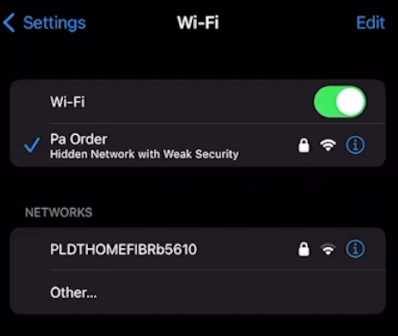
It’s noteworthy that connecting to unsecured Wi-Fi networks, especially unsecured public ones, can put your iPhone at risk for security breaches. Hackers can set up adversarial networks to secretly access your device or intercept your data. It is believed the best way to secure your internet connection was to utilize trusted, encrypted networks or a virtual private network (VPN).
You can find VPNs over at the Appstore. Most notable would be NORD VPN. Although paid, it is one of the most trusted VPNs that can add a midpoint security layer between the untrusted networks and your iPhone.
Also Read- How to Take Better Photos and Videos on Your iPhone?
Secure Your iCloud Account
Your iCloud account stores personal data, including backups, photos, and documents. Secure it by enabling two-factor authentication and regularly updating your password. Additionally, be cautious about the information you store in iCloud and consider encrypting sensitive files for an added layer of protection.
You can enable 2FA on your iCloud account by heading to Settings.
Tap your profile picture on iCloud -> Password & Security
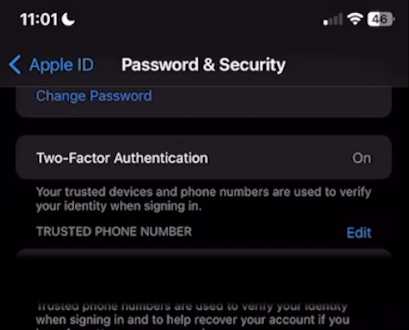
And then head to the 2FA section. That allows you to always have your iPhone with you or another iDevice to log in to your iCloud or iPhone account. This way, your Apple Ecosystem devices can be more secure than ever.
Also Read- How To Unlock Disabled iPhone 14 – 5 Quick Ways
Enable Find My iPhone
Not only can you trace your device’s location if you enable the “Find My iPhone” feature if lost or stolen. Additionally, you can remotely erase your data using this capability to prohibit illegal access. It also is an added security layer between you, your iPhone, and iDevices.
To enable it, head over to your Settings application, scroll up, and search for Find Me, and you will land in this tab. (see the illustration below)
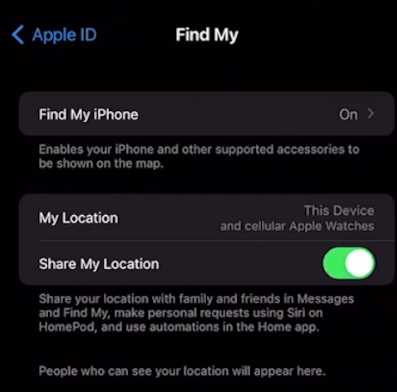
Now, enable the Find My iPhone and Share My Location.
What can you do to avoid more hacking and breaches?
Recognizing and Reporting Suspicious Activity
They believed that being alert and seeing indications of questionable activity on your iPhone was important. Watch your device for odd behavior, including unexpected pop-ups, increased battery drain, or strange programs. Take urgent action by cutting off internet access, running security checks, and aggressively contacting Apple support if you believe your iPhone has been compromised.
A crucial component of safeguarding your privacy and personal information in the digital era in a significant manner is, for the most part, the security of your iPhone. The likelihood of becoming a victim of hackers and data breaches can be significantly decreased by adhering to the best practices recommended in this article. Remember to keep your software current, use strong general and unique passwords, activate two-factor authentication, and be especially wary of basic social engineering attempts. You can significantly improve the safety and security of your iPhone experience by putting these precautions into place.
























![The Apex Legends Digital Issue Is Now Live! Apex Legends - Change Audio Language Without Changing Text [Guide]](https://www.hawkdive.com/media/5-Basic-Tips-To-Get-Better-On-Apex-Legends-1-218x150.jpg)