An iPhone being hacked are not incredibly common, but it can still occur if you are not careful enough. The hacks may occur from malware and trickster apps downloaded from the App Store. These apps will target specific device and attacks them. From here your information can be stolen in various ways.

While there is no doubt that security is a massive subject on your iPhone. Therefore, it is not hard to get your iPhone to be more secure than 99 percent of other iPhones out there.
Here in this article, we will be breaking down some of the common types of hacks, how to know if you have been hacked, and what to do about it.
How hard is it to keep your iPhone and its data safe from hackers and the wrong hands out there? It’s not hard at all.
How to Secure Your iPhone from Hackers
In this article, we will guide you through some advanced iPhone security tips. This may include turning on 2FA to switching off auto-fill. Let’s get started.
How an iPhone can be hacked
Hacking is when some unknown person gains access to private information on your device or controls it without your permission. Hacking is a broad term and lies on a gradient of bad to very serious cases. Some hackers want to make a quick and large amount by selling advertising. While others want to hurt you.
According to experts research, there are a few main types of iPhone hacks:
Some of the Suspicious websites or links
Your iPhone can be hacked just like on your computer, by clicking on a suspicious website or link. If any website looks “off” then immediately check its logos, spelling, or URL.
The other way to be safe is to try to avoid connecting to a password-free or public Wi-Fi network. This will provide an open gate to hackers accessing unencrypted traffic on your device. Or the other way is it may redirect you to a fraudulent site to access login credentials.
Sometimes you may receive messages from numbers you don’t recognize that are also suspected. Fortunately, modern smartphones are good at restricting and providing notifications of malware and ransomware.
Suspicious apps on the App Store
Apple devices have a much more sophisticated and monitored digital ecosystem when compared to Android devices.
The Computer Security and Privacy Laboratory experts at Washington University in Saint Louis have said to watch out for apps that ask for more information than they will need to function.
For instance, if you have downloaded a wallpaper or flashlight app. If the app is asking permission for your location or contact list, camera, or microphone. Unfortunately, the developers are tricking you, and giving out this information will put you in trouble.
Intimate partner hacks
Abusive partners can grab your phone and install spyware or stalker ware when you are not around. This destructive software can be used to track your location or may read your private information like texts, and your call history, or get access to emails.
This abuse can be psychologically traumatizing and destructive to someone’s personal and public life. All they need is your password and physical access to your phone. If you notice any apps that you don’t remember downloading, this could be a sign of being hacked. However, most of the time spyware apps are invisible or hidden on the home screen.
Targeted attacks
The targeted hack works like this: Hackers invade your personal space and exploit unknown flaws in iOS programming. Even the developer itself doesn’t know about it. With this knowledge, hackers will easily install malware into your phone to get data from targeted sources. The most targeted people are Journalists and activists who are at risk for this kind of hack.
How to escape from being Hacked
Three simple tips will save your iPhone from being hacked:
1# By Regularly Updating all the installed apps:
Keep your iPhone regularly updated. Doing this simple action is very necessary to fix random bugs and access exciting new features on your iPhone. Apple provides the best security for its clients and takes it very seriously. In other words, many of Apple’s updates come with security and privacy policies. Keep updating and installing them regularly. By doing this you don’t have to give a chance to target you or your personal information from the hackers.
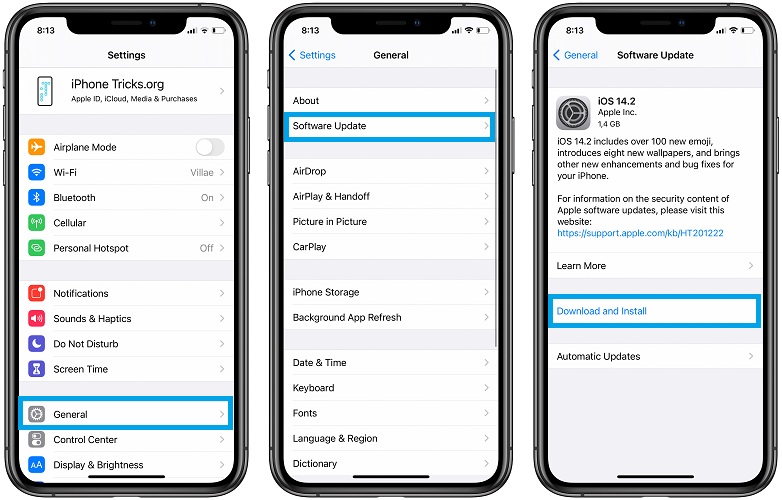
If you want to check if your iPhone has all updates installed, then go to Settings > General > Software Update. If there is any update available, download and install it.
Strong Passcode:

If you’re still rolling with 0000 or 1234 or any dumb passcode like that, first change it. While website-based attacks happen, this is the most likely way from which your data is going to leak. The leak from your iPhone is by someone picking it up and unlocking it.
Weekly Reboot :

Most iPhone vulnerabilities depend on jailbreaking the iPhone. However, the jailbreak can not survive a reboot, so adding a weekly reboot to your schedule is not a bad idea.
This not only protects your iPhone from badness but it will also speed things up a bit by clearing the RAM.
























![The Apex Legends Digital Issue Is Now Live! Apex Legends - Change Audio Language Without Changing Text [Guide]](https://www.hawkdive.com/media/5-Basic-Tips-To-Get-Better-On-Apex-Legends-1-218x150.jpg)